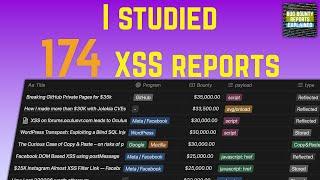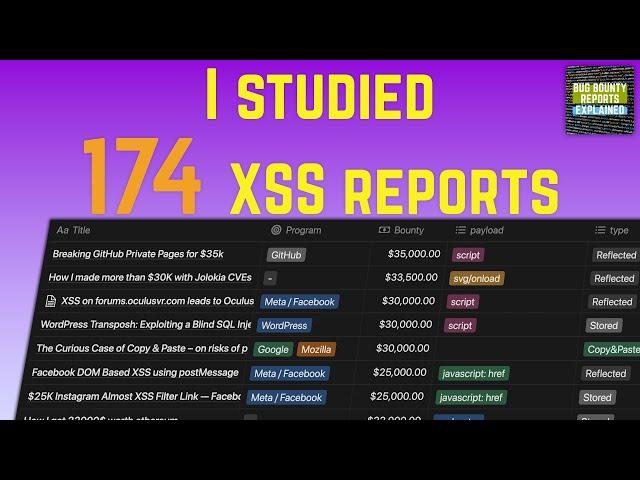
Which XSS payloads get the biggest bounties? - Case study of 174 reports
Комментарии:

Not 'E'mg tag but 'I'mg tag 😶🌫
Ответить
Fantastic video. Highly informative!
Ответить
Can you share the notion list
Ответить
What platform will u suggest for leaning bug bounty?
Ответить
is there step how to do for bug bounty each report ?
Ответить
Ten film zawiera lokowanie produktu :)
Ответить
i love you bro 🥰😍🤑
Ответить
Can You Share About the BB Automation !
Ответить
This video is Diamond. Awesome mate very well explained. Gonna signup with BBRE soon.
Ответить
Hello brother I am also doing bug bounty but not getting success
Ответить
Can you help me
Ответить
Love your vids. The other day I was messing around with a page and found an html injection, I was wondering if there was a way to escalate it to an XSS if the "=" sign is sanitized and leads me to a 403 Forbidden. Thanks!
Ответить
Can you share the template...No need database
Ответить
<svg/onload=alert()> is one of the shortest xss payloads, maybe that's why they are use more often
Ответить
Correct me if i am wrong. Can we get XSS on 404 pages.
Ответить
Would be interested in using this info as a ML training set
Ответить
Awesome analysis!!
Ответить
can you give this cheet sheet in pin comment
Ответить
just found you. veeerrry interesting channel. as someone who learns by watching a massive amount of poc videos on one topic, i like how you take the analysis deeper. finally a channel that doesnt have the redundant "how to hack" videos.
Ответить
LOVE YOUR VIDEOS
I know HTML. Currently learning JavaScript. Then I'll put my hand on portswigger labs starting from xss then idor then business logic bugs.
My Questions are:
should I watch your channel from oldest or newest or most popular?
should I continue with the approach I wrote above?

Thanks for the video =)
Ответить
This is Gold man 💥
Ответить
Better to use <img/src/onerror=alert(8)> than the quoted one
Ответить
I love you bro ❤
Ответить
Every website would be vulnerable since you are injecting the script into the console yourself. This is not valid
Ответить
Thanks!
Ответить