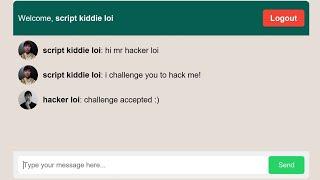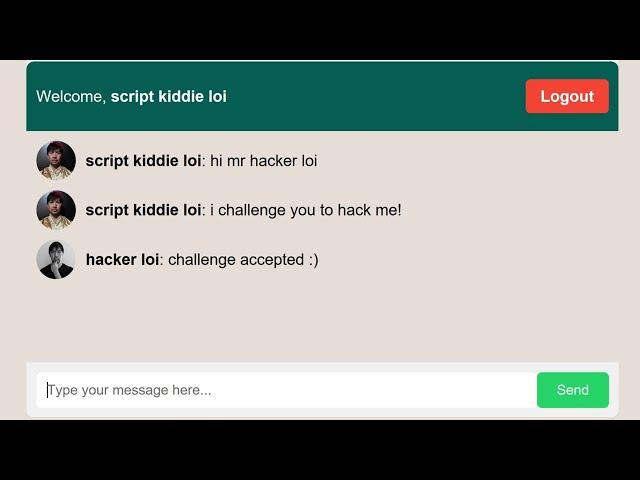
cross-site scripting (XSS) explained and demonstrated by pro hacker
Комментарии:

🎉
Ответить
First oneeeee
Ответить
Good morning Mr hackerloi
Ответить
🎉
Ответить
3rd person to comment, come hack me 😪🤒🤒😁😁
Ответить
wsg
Ответить
Cyberghost😮
Ответить
Good morning Mr hackerloi
Ответить
Comment#7!
Ответить
the concept of xss has been confusing me, this video helped me so much❤
Ответить
My mom said no ?
Ответить
yeah this stuff worked 15 years ago, now decent admins will filter input fields to remove chars needed to inject scripts
Ответить
Maybe you can try demonstrate some of CVE vulnerability that most viral and how to prevent it 😊
👇 Who agrees

Bro make videos when he has to pay his bills
Ответить
sir,I asked my mom about hacking, and she threw a spatula at me.
Ответить
God is good
Ответить
Best late Christmas gift ever, I've had issues trying to understand XSS but this gave me an idea of how it works, Thank you Mr Loi🙏
Ответить
It's not as simple as this in the real world tho😂
Ответить
🐐
Ответить
why you use windows 10 1511?
Ответить
Haha using .textContent 😂 will make it useless in JavaScript to advance for more security use a sanitizing library 🤔 about the cookies stealing 😂 you can flag it on the server side so JavaScript can't be able to manipulate it.. well i still wonder how some site prevent it while allowing formatting text 🤔 thank you for the video 🤜 i really appreciate it
Ответить
Social Engineering Toolkit?!?!? Script Kiddie detected :) You are definetely script kiddie
Ответить