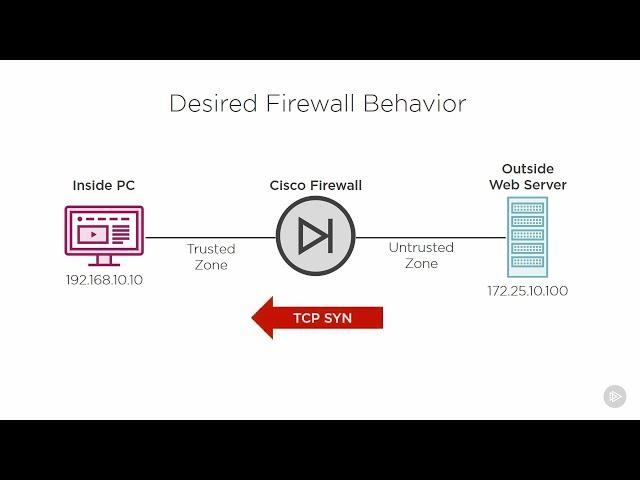
5 - Desired firewall behavior and the TCP State Table
Комментарии:
5 - Desired firewall behavior and the TCP State Table
Watch and Learn
Новые звёзды в Африке: 2 сезон, 5 серия
Звёздные Шоу
Kapa Haka | NPR
NPR
The Brutal Truth About Music Industry Connections (Hint: You're Doing It Wrong)
Recording Connection Audio Institute
400mm Long Zoom Finds something.
The Transportopia
Understanding the Rules of Football | Football
SIKANA English
Last to Leave Minecraft Creeper!
Unspeakable Studios





![Giffarine 3 Calcium[PaoYinCub Highest Grow UP ] SkyExits.com Giffarine 3 Calcium[PaoYinCub Highest Grow UP ] SkyExits.com](https://hdtube.cc/img/upload/VWVTMzdBaGdkTWo.jpg)