PWN - Bruteforcing Stack Canaries (PicoCTF 2022 #44 'buffer-overflow3')
Комментарии:

Malloc ?
Ответить
Just a programming note: byte arrays are mutable, so you don't need to completely rebuild the payload every loop. You can just build it once with 4 random bytes for the canary, then when solving for the first byte just modify the payload[offset] byte and send off payload[:offset+1], then once that's found, loop through values for payload[offset+1] and send off payload[:offset+2], etc
It's more efficient, and you don't have to keep up with the values of the positions you've found so far because they're already saved correctly in the payload

Library here
Ответить
Rax,rex,rdx, 0x86?
Ответить
Canary vuln report new video creation 🤦🤖
Ответить
Relying
Ответить
Canry 1,2vlun explain.
Ответить
Canr vilu number meine in
Ответить
Jump number cinr
Ответить
Banck employees sylres nover coming.
Ответить
Sal , change?
Ответить
Ato z
Ответить
Desc,asc date rood ing number attending time........
Ответить
Rdi ,RSI,rdx buf function using number
Ответить
Search ? number name
Ответить
Hello my friend,
at startup of video you are struggling with sscanf, it seems to me that you do didn t spotted the 2 's' : sscanf is different than scanf.
first parameter of sscanf is a pointer to a buffer which is called length in this instance, thats why your printf %d returns random number , and should be replaced by %p in order to be compliant with the type which is a pointer
thanks for all the rest

Today is my eyes chemical to facing problem nover problem chemical to face 👀 not problem
Ответить
DemJ vlyuu
Ответить
DemJ vlyuu
Ответить
DemJ vlyuu
Ответить
DemJ vlyuu
Ответить
Volume button purposes hi volume
Exl,rop reply

Volume button purposes hi volume
Exl,rop reply

Concrete wall for you breaking information
Ответить
Dive to ip address number dive files open remo light attending after again to everyone that red colour process signal to dry flowers
Ответить
Conr vlu?
Ответить
Value hai
Ответить
Rflag?
Ответить
I appreciate watching the full process of figuring it out. A lot of videos just speed through things and I’m left thinking “how did you see that so quickly?” Watching you do your thing as is also teaches the problem solving process which is just as important.
Ответить
Can we somehow exploit the fact that the local stack canary is copied from a global variable instead of brute forcing (e.g. if the canary was less "brute-forceable")?
Ответить
My solution appears to work locally, but once I connect to the remote server the 'leaking canary values' are returned in hex ('\x03\x01\x01\x01') and I get a UnicodeDecodeError: "utf-8 codec can't decode byte 0x93 in position 25: invalid start byte"
Any ideas why this is happening and how to resolve. I've googled my brains out but can't figure it out.

Heyo
Ответить
Damn my script works locally but somehow it doesn't work remotely. Could you please provide your source code to test? Thanks! :)))))
Ответить
Dude! Please do more of these. It is way more helpful to see you "bump around" (and thereby realize that you are human) than to just see you figure out complex problems in a millisecond and feel like a complete dummy when it takes me hours to figure out the same thing (if I ever do!). PLUS, we get to see your "debugging" process, which is super, super helpful. Thanks for the content as always.
Ответить
Great stuff! I'm finally getting to piece together what pwntools does. (I understand buffer overruns etc. fairly well, but these automated tools are new to me). What would be even better would be some sort of O'Reilly book or the like on it. (Yes, I'd even buy a dead tree edition.)
Ответить
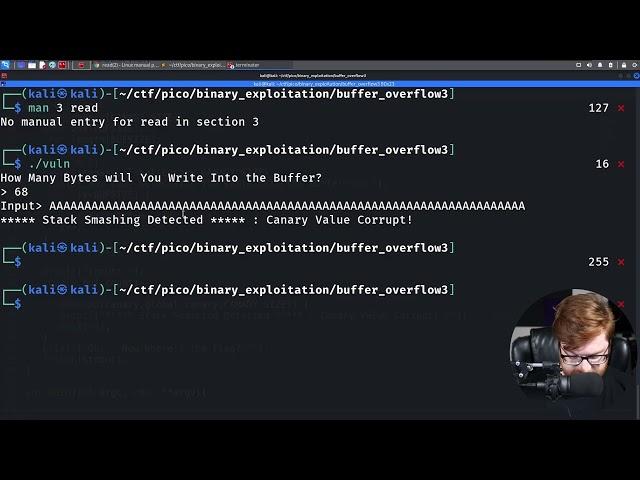
You can access the man pages of read with `man 2 read`.
This is because read is a syscall, not a library function, so it's docs are in section 2 of the manual. Section 3 is for libraries.
Hope ppl will find it helpful.
Keep up the great work!

@_JohnHammond you are amazing.
I love your way and I have learned a lot from you.
Thank you very much.

John is a Genius!!!!
Ответить
And of course it’s another “banger” video.
Ответить
Great!!! Please never stop!!!!
Ответить
Can you please have a go on device called deeper connection Pico DPN (like VPN) and they are claiming that nobody can hack it . Since you are very creative i was wondering if u wanna have a go ? Thanks you’re great 👍
Ответить
Should we attempt buffer overflow challenges without checking the source code?
Ответить
You are the best dude Keep up 🔥🔥🔥
Ответить
Yt algo bump
Ответить
Ah, now we're getting into the interesting stuff!
Ответить
Disgusting
Ответить
Great video, really learned a lot👍
Ответить