USENIX Security '20 - Everything Old is New Again: Binary Security of WebAssembly
Everything Old is New Again: Binary Security of WebAssembly
Daniel Lehmann, University of Stuttgart; Johannes Kinder, Bundeswehr University Munich; Michael Pradel, University of Stuttgart
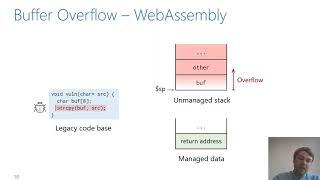
WebAssembly is an increasingly popular compilation target designed to run code in browsers and on other platforms safely and securely, by strictly separating code and data, enforcing types, and limiting indirect control flow. Still, vulnerabilities in memory-unsafe source languages can translate to vulnerabilities in WebAssembly binaries. In this paper, we analyze to what extent vulnerabilities are exploitable in WebAssembly binaries, and how this compares to native code. We find that many classic vulnerabilities which, due to common mitigations, are no longer exploitable in native binaries, are completely exposed in WebAssembly. Moreover, WebAssembly enables unique attacks, such as overwriting supposedly constant data or manipulating the heap using a stack overflow. We present a set of attack primitives that enable an attacker (i) to write arbitrary memory, (ii) to overwrite sensitive data, and (iii) to trigger unexpected behavior by diverting control flow or manipulating the host environment. We provide a set of vulnerable proof-of-concept applications along with complete end-to-end exploits, which cover three WebAssembly platforms. An empirical risk assessment on real-world binaries and SPEC CPU programs compiled to WebAssembly shows that our attack primitives are likely to be feasible in practice. Overall, our findings show a perhaps surprising lack of binary security in WebAssembly. We discuss potential protection mechanisms to mitigate the resulting risks.
View the full USENIX Security '20 program at https://www.usenix.org/conference/usenixsecurity20/technical-sessions
Daniel Lehmann, University of Stuttgart; Johannes Kinder, Bundeswehr University Munich; Michael Pradel, University of Stuttgart
WebAssembly is an increasingly popular compilation target designed to run code in browsers and on other platforms safely and securely, by strictly separating code and data, enforcing types, and limiting indirect control flow. Still, vulnerabilities in memory-unsafe source languages can translate to vulnerabilities in WebAssembly binaries. In this paper, we analyze to what extent vulnerabilities are exploitable in WebAssembly binaries, and how this compares to native code. We find that many classic vulnerabilities which, due to common mitigations, are no longer exploitable in native binaries, are completely exposed in WebAssembly. Moreover, WebAssembly enables unique attacks, such as overwriting supposedly constant data or manipulating the heap using a stack overflow. We present a set of attack primitives that enable an attacker (i) to write arbitrary memory, (ii) to overwrite sensitive data, and (iii) to trigger unexpected behavior by diverting control flow or manipulating the host environment. We provide a set of vulnerable proof-of-concept applications along with complete end-to-end exploits, which cover three WebAssembly platforms. An empirical risk assessment on real-world binaries and SPEC CPU programs compiled to WebAssembly shows that our attack primitives are likely to be feasible in practice. Overall, our findings show a perhaps surprising lack of binary security in WebAssembly. We discuss potential protection mechanisms to mitigate the resulting risks.
View the full USENIX Security '20 program at https://www.usenix.org/conference/usenixsecurity20/technical-sessions
Тэги:
#usenix #technology #conference #open_accessКомментарии:
Canibus - SuperLuminal Travel (Full version)
RTJ2INFINITYPROMO
Pilatus PC-6 Technic info. HD Movie by Heliasz
Jacek Heliasz
Tina's Triumph Trident - MS Affects Riding
NothingToProve
I tried "Swedish Death Cleaning" and it CHANGED EVERYTHING!
That Awkward Mom