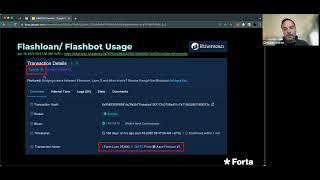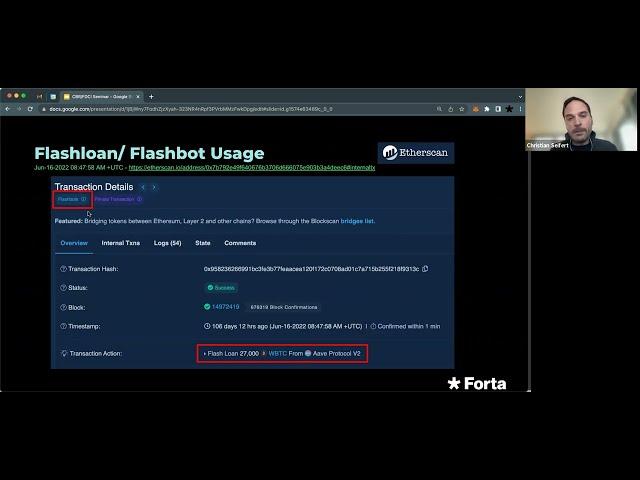
"Comprehensive Security Strategy in Web3" (Christian Seifert)
This talk reviews recent web3 attacks, draws parallels to web2 security, and then outlines a comprehensive security strategy that spans from pre deployment steps (eg, auditing) to post deployment steps (monitoring and incident response). The talk provides an overview of these topics and highlights future research opportunities.
Комментарии:
"Comprehensive Security Strategy in Web3" (Christian Seifert)
Stanford CBR FDCI
Adolf Hitler Speech in 1935
Upscaled History
The Future of British Politics after BREXIT
Hellenic Observatory, LSE
半夜睡覺腳抽筋!最重要的自救方法,如何居家物理治療?
光合物理治療所
CAM00007.mp4
Anthony Krouse
Приписнов Роман "Блокада"
Людмила Ганина