Access Control Strategies
Role-based access control (RBAC) vs. Attribute-based access control (ABAC)
IBM Technology
8K
27,102
5 месяцев назад
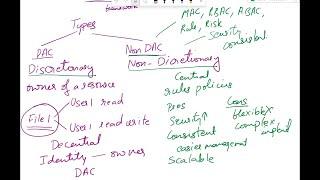
Explain Access Control Models| Discretionary DAC, Mandatory MAC, RBAC, Rule, Attribute, Risk based
CyberPlatter
14K
47,329
1 год назад
Cybersecurity Architecture: Five Principles to Follow (and One to Avoid)
IBM Technology
137K
457,131
1 год назад
Access Control | Information Security Management Fundamentals Course
Instructor Alton
7K
23,347
4 года назад
Whiteboard Wednesday - Role-Based Access Control: What is It? What are the Benefits?
TechGrid
1K
4,427
7 лет назад
Security Masterclass – Learn strategies to deploy and manage security from N-sight
N-able
24
81
2 дня назад
Kubernetes Security Best Practices you need to know | THE Guide for securing your K8s cluster!
TechWorld with Nana
60K
199,194
2 года назад
Jenkins : How to control Role based access in jenkins for users and groups #jenkins #accesscontrol
DevOps - Free Tutorials
3K
9,345
1 год назад
Сейчас ищут
Access Control Strategies
A Turtle S Tale 2 Sammy S Escape From Paradise
Subtitulada Al Español
Pancake House
Andilex Settings
Trendpiler
Jack Wiley
Math Help
500Whp
Shadiego
Gambling Market Analysis
Evening Weather Forecast
Kabar Madura Hari Ini
Nyvarsity Sports
One Piece Katakuri Music
流浪地球
Сербский Вайб
Adedè
Nsys Maharashtra
سمی
Cody Webster Professional Bullfighter
How To Calligraphy
董志成
Афоризмы Брайан Трейси
Ҳидоят Тв
Texas Waterfowl Hunting
One Piece Ost Katakuri Theme
Ai Motivation
Amber Sparks Kasper
Gleise
Запись
Latest African Fashion
Access Control Strategies. Смотреть видео: Role Based Access Control RBAC Vs Attribute Based Access Control ABAC, Explain Access Control Models Discretionary DAC Mandatory MAC RBAC Rule Attribute Risk Based, Maximizing Access Control Key Strategies For Effective Security, Cybersecurity Architecture Five Principles To Follow And One To Avoid.